In a variety of Support scenarios, it is usually necessary to take a network trace and observe communication from client to virtual server. In many scenarios, the communication is encrypted with SSL, and because of client security regulations it is not always possible to share the Private key (to decrypt the SSL traffic). With this procedure, you only need the session keys and not the original Private key to decrypt the network traffic.
So this is what you need perform this action:
- Wireshark
- SSL encrypted virtual server
- Private key
1. Start a trace and save it somewhere…
2. Download Wireshark and open your trace:
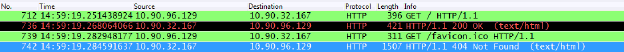
As you see here, all trafic in encrypted (SSL)
3. Select >Edit > Preferences > Protocols > SSL > RSA Keys list > Edit, to decrypt the trace (using the private key) in Wireshark:
Enter IP of your Netscaler AGVIP, Port 443, http as a protocol and Link to your Certificate key… Then hit “Apply”

The SSL traffic should be decrypted by now and evrything will be displayed in open text…
4. Export the Session Keys to let a thrid-party have access to the data included in the network trace, without sharing the Private Key with anyone (for security reasons)
In Wireshark, select File > Export SSL Session Keys,
and save the file somewhere… You should now have a file with “RSA Session-ID: [string of characters] Master-Key: [string of characters]”. This file can be used to decrypt the trace, in place of the private key.
5. Open another Wireshark session, and attempt to use the Session keys you just exported to decrypt the same trace (session).
In Wireshark, select Edit > Preferences > Protocols > SSL > (Pre)-Master-Secret log filename
and select the exported Session Keys and You’ll now have visibility of the same decrypted traffic, without using the Private key directly.


