The Netscaler VPX appliances running firmware version 10.5 57.7 nc and above does support TLS protocol versions 1.1 and 1.2. This is a huge improvement on SSL security.
So let’s start by a simpel test by navigating here and enter the public FQDN of your AGVIP and hit “Submit”
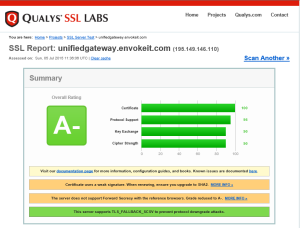
Here are the results… A C score is not good enough…
As you see above, there are some SSL security issues we need to adress:
1. The server accepts the RC4 Cipher
2. The server does not support Forward Secrecy
3. The Server is valnerable to the poodle attack
So how can we improve this and hopofully hit an A- or maybe even better a A+ score insteadof the current C
(If you prefer to jump directly to the configuration needed to hit a A+ score, step 8 includes all CLI code needed to achieve your goal)
1. Upgrade the Netscaler Firmware: If you did not upgrade the Netscaler firmware to version version 10.5 57.7, please hurry and do that!
2. Disable SSLv3 to prevent POODLE attacks:
Log on to your Netscaler VPX and navigate to NetScaler Gateway – NetScaler Gateway Virtual Servers
Edit SSL Parameters by disabling SSLv3 and enabling TLSv11 & TLSv12 as shown below
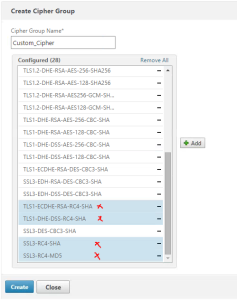
3. Create a custom Cipher Group
Well! Navigate to Traffic Management – SSL – Cipher Groups
Highlight the DEFAULT cipher group and click Add.
Scroll down and remove all RC4 ciphers you find (should be four of them and located at the bottom of the table) and hit Create
Note!
The following list of Ciphers will support all modern browsers and the Citrix Receivers.
TLS1-DHE-DSS-AES-256-CBC-SHA
TLS1-DHE-DSS-AES-128-CBC-SHA
TLS1-DHE-RSA-AES-256-CBC-SHA
TLS1-DHE-RSA-AES-128-CBC-SHA
TLS1-ECDHE-RSA-DES-CBC3-SHA
TLS1-ECDHE-RSA-AES128-SHA
TLS1-ECDHE-RSA-AES256-SHA
TLS1.2-AES128-GCM-SHA256
TLS1.2-AES256-GCM-SHA384
TLS1.2-DHE-RSA-AES128-GCM-SHA256
TLS1.2-DHE-RSA-AES256-GCM-SHA384
TLS1.2-ECDHE-RSA-AES128-GCM-SHA256
TLS1.2-ECDHE-RSA-AES256-GCM-SHA384
TLS1.2-ECDHE-RSA-AES-128-SHA256
TLS1.2-ECDHE-RSA-AES-256-SHA384
TLS1.2-AES-256-SHA256
TLS1.2-AES-128-SHA256
TLS1.2-DHE-RSA-AES-128-SHA256
TLS1.2-DHE-RSA-AES-256-SHA256
Now navigate back to NetScaler Gateway – NetScaler Gateway Virtual Servers and edit your AGVIP by adding the SSL Ciphers option from the right panel and bind the custom Cipher Group we just created…
If you get any kind of warning regarding “usable ciphers” like the one shown below, just ignore it by hitting OK..
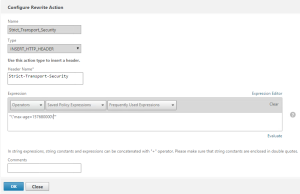
4. Enable Strict Transport Security (STS) by creating a rewrite policy and binding it to your SSL Virtual Server (AGVIP) as a respons rewrite (Not request)
We would like to add a header that instruct the client to use “https” only. By doing this you are preventing man in the middle attacks that strip the SSL conversation when the client has seen the header.
Start by creating a rewrite action:
Navigate to NetScaler – AppExpert – Rewrite – Rewrite Actions
add rewrite action Strict_Transport_Security insert_http_header Strict-Transport-Security “\”max-age=157680000\””
and a rewrite policy:
Navigate to NetScaler – AppExpert – Rewrite – Rewrite Policies
add rewrite policy Strict_Transport_Security_Pol “true” Strict_Transport_Security
5. Enable PFS (Perfect Forward Secrecy)
Perfect Forward Secrecy protect a vpn session from being decrypted when the server key becomes compromised.
To enabled PFS we need to Create a Diffie-Hellman (DH) key
Navigate to NetScaler – Traffic Management – SSL
Under Tools Create Diffie-Hellman (DH) key… Or use the CLI by entering : create ssl dhparam DHKey 2048 -gen 2
The DH key is stored in the /nsconfig/ssl directory on the appliance by default…
Now navigate back to NetScaler – NetScaler Gateway – NetScaler Gateway Virtual Servers and edit SSL Parameters by enabling DH Param
Note! The Enable DH Key Expire Size Limit option enables the use of NIST recommended (NIST Special Publication 800-56A) bit size for private-key size. For example, for DH params of size 2048bit, the private-key size recommended is 224bits. This is rounded-up to 256bits.
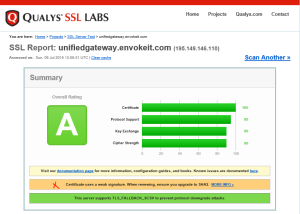
6. Now Let’s perform a New SSL test…
As you can see above we did gain some security improvement score moving from (C to A-) and that is not bad at all 🙂
But there is always room for SSL improvements and our goal is to maintain the highest possible score.
To acheive that we need to make use of a smaller set of SSL Ciphers, therefore we need to edit our custom SSL Cipher Group by removing additional Ciphers so it just contains the following ones…
TLS1.2-ECDHE-RSA-AES-128-SHA256
TLS1-ECDHE-RSA-AES256-SHA
TLS1-ECDHE-RSA-AES128-SHA
TLS1-DHE-RSA-AES-256-CBC-SHA
TLS1-DHE-RSA-AES-128-CBC-SHA
TLS1-AES-256-CBC-SHA
TLS1-AES-128-CBC-SHA
SSL3-DES-CBC3-SHA (Use this Cipher only if you still have users running IE8 on WinXP)
A new test using the updated Cipher Group gave me the results below…
We moved from A- to A and that is an improvement. The only parameter preventing me from hitting an A+ is the weakness of my Certificate signature hash algoritm (SHA1).
When renewing, I’ll make sure to upgrade it to SHA2 and I’m pretty sure I’ll be able to reach my goal and hit the A+ score 🙂
Note! If you are using the new UnifiedGateway feature (Netscaler 11), do not forget to perform the same steps described above on the public ContentSwitch vServer as well 🙂
7. Consider allowing secure renegotiation
The default setting is to deny “ALL” renegotiation, including secure. Preventing all renegotiation will result in an “A-“
You can allow secure renegotiation initiated by both NetScaler and client by choosing to block only “NONSECURE”, or only allow NetScaler initiated secure renegotiation by selecting the “FRONTEND_CLIENT” option.
Allowing insecure renegotiation, which you absolutely shouldn’t do, will result in an “F.”
8. Configuration code on Netscaler
add ssl cipher Secure-Cipher-Group
bind ssl cipher Secure-Cipher-Group -cipherName TLS1.2-ECDHE-RSA-AES256-GCM-SHA384
bind ssl cipher Secure-Cipher-Group -cipherName TLS1.2-ECDHE-RSA-AES128-GCM-SHA256
bind ssl cipher Secure-Cipher-Group -cipherName TLS1.2-ECDHE-RSA-AES-256-SHA384
bind ssl cipher Secure-Cipher-Group -cipherName TLS1.2-ECDHE-RSA-AES-128-SHA256
bind ssl cipher Secure-Cipher-Group -cipherName TLS1-ECDHE-RSA-AES256-SHA
bind ssl cipher Secure-Cipher-Group -cipherName TLS1-ECDHE-RSA-AES128-SHA
bind ssl cipher Secure-Cipher-Group -cipherName TLS1.2-DHE-RSA-AES256-GCM-SHA384
bind ssl cipher Secure-Cipher-Group -cipherName TLS1.2-DHE-RSA-AES128-GCM-SHA256
bind ssl cipher Secure-Cipher-Group -cipherName TLS1-DHE-RSA-AES-256-CBC-SHA
bind ssl cipher Secure-Cipher-Group -cipherName TLS1-DHE-RSA-AES-128-CBC-SHA
bind ssl cipher Secure-Cipher-Group -cipherName TLS1-AES-256-CBC-SHA
bind ssl cipher Secure-Cipher-Group -cipherName TLS1-AES-128-CBC-SHA
bind ssl cipher Secure-Cipher-Group -cipherName SSL3-DES-CBC3-SHA
unbind ssl vserver Name-Of-Your-NetScaler-Gateway-vServer -cipherName DEFAULT
bind ssl vserver Name-Of-Your-NetScaler-Gateway-vServer -cipherName Secure-Cipher-Group
bind ssl vserver Name-Of-Your-NetScaler-Gateway-vServer -eccCurveName ALL
set ssl parameter -denySSLReneg FRONTEND_CLIENT
add rewrite action STS-Header-Insertion-Action insert_http_header Strict-Transport-Security “\”max-age=157680000\””
add rewrite policy STS-Header-Insertion-Policy true STS-Header-Insertion-Action
bind vpn vserver Name-Of-Your-NetScaler-Gateway-vServer -policy STS-Header-Insertion-Policy -priority 100 -gotoPriorityExpression NEXT -type RESPONSE